Evaluation of Some Windows and Linux Security Tools
GFI LANguard, Nessus, Snort, Base, ACID, Rman, SnortCenter, OSSEC, Sguil
Nonfiction, Computers, Networking & Communications, Computer Security, Operating Systems, Application Software| Author: | Dr. Hidaia Alassouli | ISBN: | 1230002179971 |
| Publisher: | Dr. Hidaia Mahmood Alassouli | Publication: | February 26, 2018 |
| Imprint: | Language: | English |
| Author: | Dr. Hidaia Alassouli |
| ISBN: | 1230002179971 |
| Publisher: | Dr. Hidaia Mahmood Alassouli |
| Publication: | February 26, 2018 |
| Imprint: | |
| Language: | English |
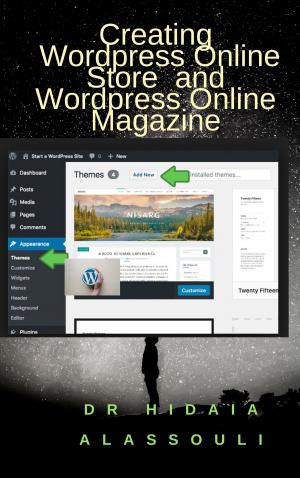
The paper evaluates some the security tools. Top security tools can be found in http://sectools.org/. Most important vulnerabilities in Windows and Linux can be found in www.sans.org/top20/. The paper covers the installation and configuration of the following security tools:
LANguard
Nessus
Snort
BASE
ACID
Rman
SnortCenter.
OSSEC
Sguil
Keywords: Vulnerability Assessment Tools, Intrusion Detection Tools, LANguard, Nessus, Snort, BASE, Rman, OSSEC, Sguil.
Author: Dr. Hidaia alassouli
Email: hidaia_alassouli@hotmail.com
The paper evaluates some the security tools. Top security tools can be found in http://sectools.org/. Most important vulnerabilities in Windows and Linux can be found in www.sans.org/top20/. The paper covers the installation and configuration of the following security tools:
LANguard
Nessus
Snort
BASE
ACID
Rman
SnortCenter.
OSSEC
Sguil
Keywords: Vulnerability Assessment Tools, Intrusion Detection Tools, LANguard, Nessus, Snort, BASE, Rman, OSSEC, Sguil.
Author: Dr. Hidaia alassouli
Email: hidaia_alassouli@hotmail.com